Table Of Contents
What Is Information Leakage?
Information leakage in finance refers to the unauthorized release or spread of sensitive financial information to external parties, which can lead to market manipulation and financial losses. It occurs through various means, such as hacking, insider trading, or accidental exposure of confidential data.
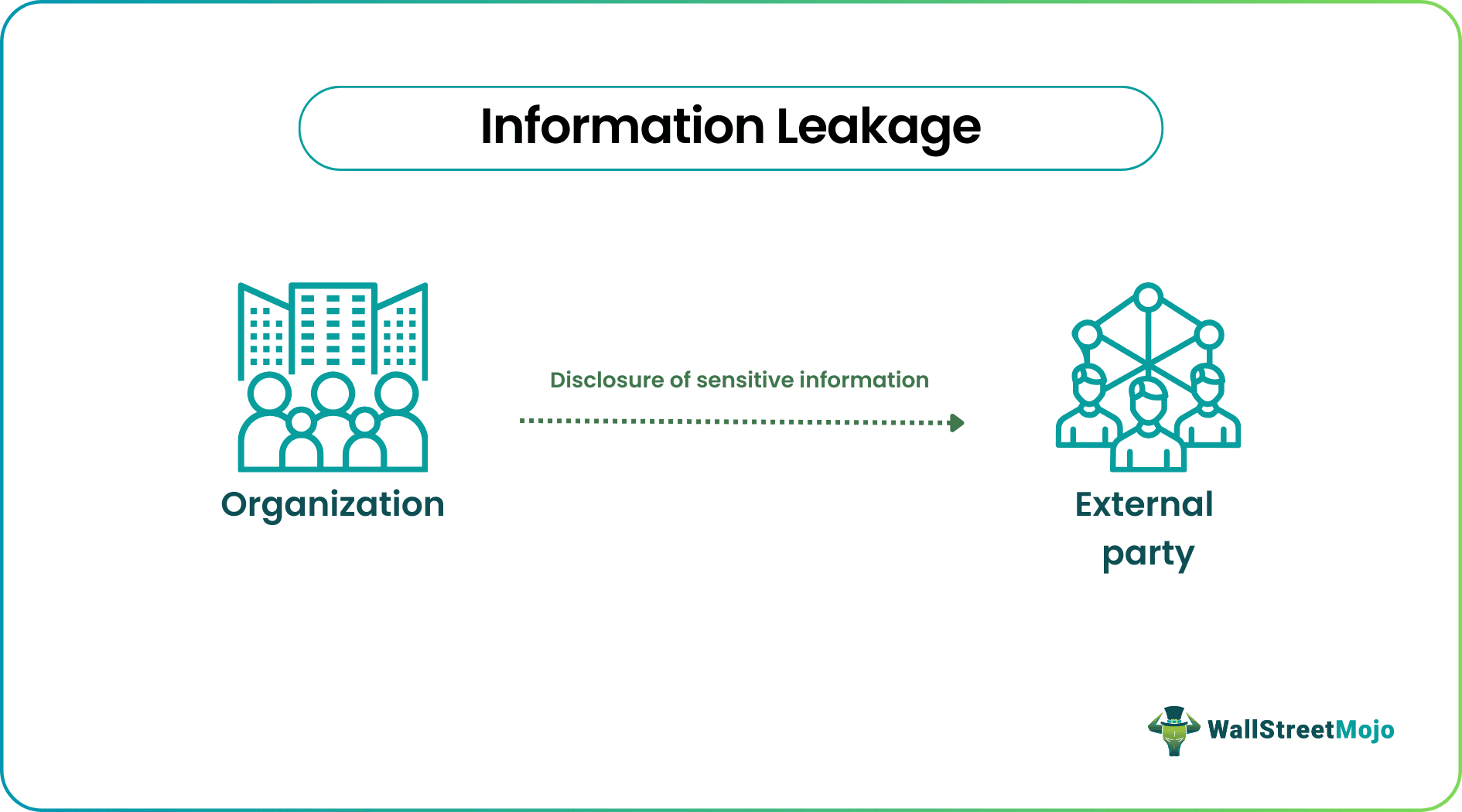
The goal is to ensure that financial information is only shared with authorized parties and its distribution is controlled and secured to minimize the risk of unauthorized access or manipulation. It can include information related to investment strategies, earnings results, mergers and acquisitions, and other critical business matters.
Table of contents
- What Is Information Leakage?
- In finance, information leakage refers to the unauthorized disclosure or dissemination of sensitive financial information to parties outside an organization, which can result in market manipulation and financial losses.
- It can happen through various means, such as media leaks, insider trading, or unintentional disclosure.
- Companies can avoid it through stricter security measures, communication protocols, employee training, and trading regulations.
- The goal is to minimize the risk of unauthorized access or manipulation by ensuring that financial information is only shared with authorized parties and that its distribution is controlled and secure.
Information Leakage Explained
Information leakage in finance refers to the unauthorized release of sensitive or confidential information that can affect financial markets or influence investment decisions. This can include insider information about a company's financial performance, upcoming mergers or acquisitions, or market rumors.
Information leakage can occur through various channels, such as media leaks, insider trading, or accidental disclosure. Using this information for personal gain is illegal and can result in significant fines, imprisonment, and damage to reputation. Financial organizations must implement strict information security measures to prevent information leakage and protect the interests of their clients.
It can occur due to various reasons, including:
- Insider Trading: This is the illegal practice of using inside information for personal gain by trading in securities. Insider trading can involve employees, executives, or others with access to non-public company information disclosing them to external sources.
- Media Leaks: This refers to the unauthorized release of confidential information to the media, either through a leak or a deliberate leak. The information may be related to a company's financial performance, upcoming mergers or acquisitions, or other sensitive information.
- Accidental Disclosure: This refers to the accidental release of sensitive information due to human error, such as a misaddressed email, a lost laptop, or a data breach.
- Market Rumors: This refers to the spread of false or unverified information through the market, which can impact investment decisions. Various sources, including traders, analysts, or other market participants, can generate market rumors.
Many traders use Saxo Bank International to research and invest in stocks across different markets. Its features like SAXO Stocks offer access to a wide range of global equities for investors.
Causes
There are several causes of information leakage in finance, including:
- Human Error: This can occur through accidental disclosure, such as misaddressed emails, lost laptops, or careless handling of sensitive information.
- Insider Trading: This occurs when individuals with access to non-public information, such as employees, executives, or others, use that information for personal gain by trading in securities.
- Lack of Information Security Measures: This refers to the failure of organizations to implement adequate measures to protect sensitive information, such as data encryption, access controls, and regular security audits.
- Malicious Actors: This includes individuals who deliberately leak confidential information for personal gain. These can be the competitors, hackers, or employees seeking to harm the company.
- Market Rumors: This refers to the spread of false or unverified information through the market, which can impact investment decisions.
- Poor Communication Practices: This refers to the failure of organizations to establish clear and effective communication protocols, leading to the unauthorized release of sensitive information.
- Regulatory Weaknesses: This refers to the lack of strong regulations or ineffective enforcement of regulations, which can lead to information leakage.
Examples
Let us look at information leakage examples to understand the concept better:
Example #1
One example of information leakage in finance is the 2008 case of Raj Rajaratnam. He was a hedge fund manager convicted of insider trading. Rajaratnam was found to have traded on inside information that he received from corporate executives, investment bankers, and others. The information included confidential details about mergers and acquisitions, earnings, and other financial performance. Rajaratnam made tens of millions of dollars in illegal profits due to his insider trading. He was sentenced to 11 years in prison and ordered to pay a $10 million fine.
This case highlights the serious consequences of information leakage and the importance of preventing it. It also warns others who might be tempted to engage in insider trading or misuse confidential information for personal gain. Regulators and organizations must be vigilant in preventing information leakage and enforcing regulations to ensure fair and transparent financial markets.
Example #2
Retail giant Target agreed to pay $18.5 million to settle claims by 47 states and the District of Columbia, resolving a multi-state investigation into a massive data breach that occurred in late 2013. Led by the attorneys general of Connecticut and Illinois, the investigation found that cyber attackers accessed Target's gateway server using stolen credentials from a third-party vendor. This breach, one of the largest to hit a U.S. retailer, resulted in the theft of data from up to 40 million credit and debit cards of holiday season shoppers in 2013. Per the report, California would receive the largest share of the settlement, totaling over $1.4 million.
Target has settled with financial institutions and states but is still finalizing a consumer settlement, including a class action lawsuit settlement. As part of this settlement, Target is obligated to implement advanced security measures to protect customer information. This includes appointing an executive to oversee an extensive information security program and advise the CEO and board. Additionally, the company must hire an independent third party to conduct a comprehensive security assessment and enhance card information encryption or protection to render it useless if stolen.
Prevention
Here are some steps that organizations can take to prevent information leakage:
- Implement Information Security Measures: This includes data encryption, access controls, firewalls, and regular security audits.
- Establish Clear Communication Protocols: Organizations should establish clear communication protocols to ensure that only authorized individuals should receive sensitive information.
- Regular Employee Training: Regular training on information security and the importance of protecting sensitive information can help employees understand their role in preventing information leakage.
- Monitor for Signs of Information Leakage: Organizations should monitor for signs of information leakage, such as unusual patterns of insider trading or media leaks.
- Implement Strong Insider Trading Regulations: Regulators should enforce strict insider trading regulations to prevent the illegal use of inside information for personal gain.
- Conduct Regular Security Audits: Regular security audits can help organizations identify vulnerabilities and prevent information leakage.
Disclosure: This article contains affiliate links. If you sign up through these links, we may earn a small commission at no extra cost to you.
Frequently Asked Questions (FAQs)
An information leakage attack is a security breach in which sensitive information is inadvertently disclosed through non-secure channels, such as an open network or weakly protected file storage system. An attacker can use this information to gain unauthorized access to sensitive data, steal identities, or commit other malicious activities.
The effects of information leakage can be far-reaching and damaging for individuals and organizations. Some of the potential consequences include the following:
- Identity theft: Information such as Social Security numbers, addresses, and other personal data can be used to steal a person's identity.
- Financial loss: Information about bank accounts, credit cards, and other financial details can be used to commit fraud or steal money.
- Business damage: Confidential business information, such as trade secrets, can be used by competitors to gain an advantage.
There are several ways to detect information leakage, including the following:
- Network monitoring: Monitoring network traffic for unusual or unauthorized data transfers can help detect information leaks.
- Log analysis: Analyzing log files from systems, such as firewalls, servers, and databases, can provide insights into potential information leaks.
- Data loss prevention (DLP) tools: DLP tools can scan for sensitive data being transmitted over networks or stored on devices and alert administrators to any potential information leaks
Recommended Articles
This article has been a guide to what is Information Leakage. Here, we explain the topic in detail, including its examples, prevention, and causes. You may also find some useful articles here -