Table Of Contents
What Are Cybersecurity Threats?
Cybersecurity threats are malicious attacks or unauthorized access to computer systems, networks, or devices. Some biggest cybersecurity threats include viruses, malware, phishing scams, denial of service attacks, and data breaches. These threats can result in the loss of sensitive information, damage to infrastructure, and financial loss.
It aims to gain unauthorized access to, disrupt, or steal sensitive information from a computer system or network. The ultimate goal of these threats is to gain financial benefit, spying, social engineering, access sensitive information, disrupt business operations, or disrupt critical infrastructure.
Key Takeaways
- Cybersecurity threats include hostile assaults and illegal access to computer systems, networks, and devices.
- These threats come in many forms, such as malware, ransomware, phishing, DDoS attacks, APTs, IoT threats, social engineering, insider threats, crypto-jacking, and cloud security threats.
- Cybersecurity threats can have severe consequences, from data breaches to financial losses to physical damage.
- These threats are constantly evolving, so staying informed and updated on the latest threats and best practices for protecting oneself and one's organization is essential.
Cybersecurity Threats Explained
Cybersecurity threats are an invasion that seeks to jeopardize the safety of a computer network or system. They can pose a significant threat to organizations and individuals because they can lead to many negative consequences. These threats' potential impacts include data theft, system downtime, damage to equipment, loss of intellectual property, increased cost, and legal compliance issues.
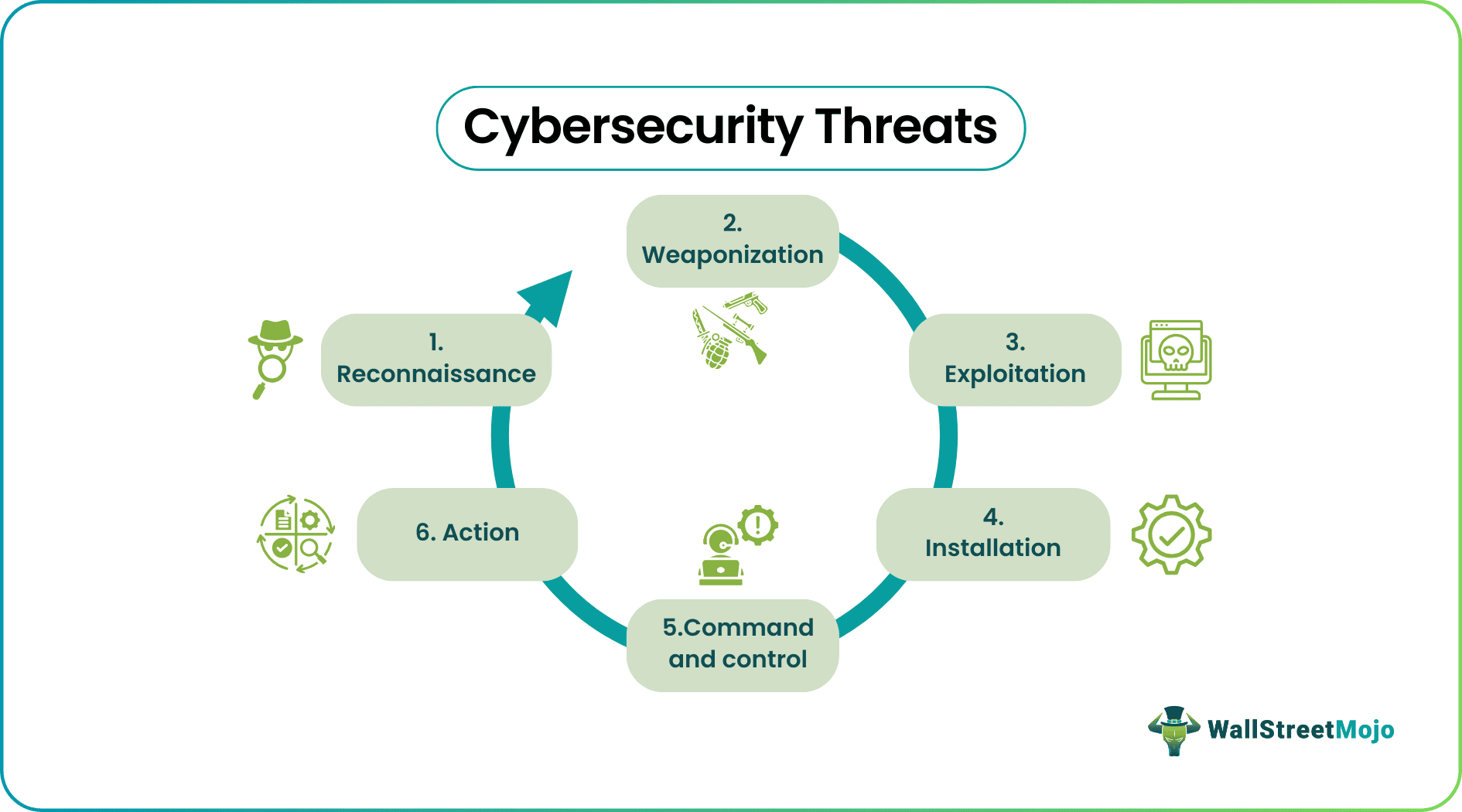
The process of cybersecurity threats typically follows these general steps:
- Reconnaissance: Attackers gather information about their target, like identifying vulnerabilities and weaknesses in the system.
- Weaponization: Attackers create or obtain tools and techniques to exploit vulnerabilities and gain access to the target system.
- Delivery: Attackers use various methods to deliver weaponized tools and techniques to the target system, like email attachments, malicious websites, or software vulnerabilities.
- Exploitation: Attackers use the delivered tools and techniques to gain access to and control the target system.
- Installation: Attackers install malware or other malicious software on the target system to maintain control and access to the system.
- Command And Control: Attackers use the installed malware to remotely control the target system, exfiltrate data, or cause damage.
- Actions On Objectives: Attackers use their control over the system to achieve goals like stealing sensitive information, disrupting operations, or extorting money.
Choosing a reliable web hosting provider with strong security infrastructure, like Hostinger, can play a vital role in reducing cyber risks and ensuring data protection.
Sources
There are many potential sources of cybersecurity threats, including:
- Hackers: Individuals or groups who attempt to gain unauthorized access to networks, computer systems, or devices for personal gain or to cause harm.
- Malware: Malicious software like viruses, trojans, and ransomware, damages or steal information from computer systems.
- Phishing: Attempts to trick individuals into providing sensitive information like financial information or login credentials.
- Social Engineering: Using psychological manipulation to divulge sensitive information or perform actions they usually wouldn't.
- Insiders: Employees or contractors with legitimate access to an organization's systems can use that access to steal or damage information.
- IoT and Operational Technologies: Cybersecurity threats often come from insecure Internet of Things (IoT) devices and operational technologies (OT). It connects to a network like industrial control system (ICS).
- State-sponsored actors: Cyberattacks that foreign governments or organizations sponsor to steal sensitive information, disrupt critical infrastructure, or for other malicious purposes.
Types
Several types of cybersecurity threats include:
- Malware: Software designed to harm or exploit a computer system.
- Ransomware: Malware that encrypts a user's files and demands money in exchange for the decryption key.
- Phishing: A form of social engineering in which an attacker poses as a trusted entity to trick a user into providing sensitive information.
- Distributed Denial of Service (DDoS) attacks: DDoS attacks flood websites or network resources with high volumes of traffic from multiple sources, causing service disruption or complete downtime.
- Advanced Persistent Threats (APTs): A cyberattack in which a cybercriminal forms a longstanding presence on a victim's network to steal sensitive data.
- IoT threats: These target Internet of Things (IoT) devices, like smart homes, connected cars, and medical devices.
- Social Engineering: Tricking people into divulging sensitive information or performing actions that may compromise their security.
- Insider cybersecurity threats: Here, an employee of an organization causes harm to the employer's security.
- Crypto-jacking: Unauthorized use of someone's device to mine cryptocurrency.
- Cloud Security Threats are unauthorized access and breaches targeting cloud-based systems and data.
Examples
Let us go through some examples of it.
Example #1
A hypothetical example of a cyber attack could be as follows:
- The attacker, a member of a hacking group, begins by researching a large retail company and its online presence. First, they identify the company's primary website and web server's IP address.
- The attacker uses a network scanning tool to probe the server for vulnerabilities. They find that the server is running an outdated version of a popular content management system (CMS) with a known security vulnerability.
- The attacker crafts a tailored exploit for this vulnerability and launches it against the server.
- The exploit is booming, and the attacker gains access to the server. They proceed to upload a malicious script to the server. It creates a back door that allows the attacker to access the server at any time remotely.
- The attacker uses the back door to access the server's database and steal sensitive information, like customer names, addresses, and credit card numbers.
- The attacker sells this information on the dark web. This prompts financial fraud. The retail company now deals with the damage caused by the attack, including the loss of sensitive customer data and damage to its reputation.
Example #2
One real-life example of a cybersecurity threat is the WannaCry ransomware attack in May 2017. This malware spread rapidly through networks, encrypting files on infected computers and demanding payment in exchange for the decryption key. The attack affected about 200,000 computers in 150 countries. Victims included hospitals, businesses, and governments. The attack propagated quickly. This resulted from a vulnerability in the Microsoft Windows operating system that the attackers had exploited.
Impact
Cybersecurity threats can impact individuals, organizations, and entire industries. Some of the potential impacts include:
- Loss or theft of personal or sensitive information like financial data or unique identification numbers.
- Damage to computer systems or networks, resulting in downtime and lost productivity.
- A financial loss like fraudulent activities or extortion.
- Reputational damage results from a data breach or other security incident.
- National security threats through breaches of critical infrastructure or government systems.
- Disruption of essential healthcare, transportation, and communication services.
Individuals and organizations must protect themselves from common cybersecurity threats by implementing security measures and best practices.
How To Prevent?
Steps for the prevention of cybersecurity threats can be:
- Keep software and operating systems up to date: This includes the computer's operating system and software installed, like web browsers and antivirus programs.
- Use strong and unique passwords for all accounts: Passwords should be 12 characters long and include a mix of numbers, letters, and symbols. Avoid using easily guessable information like your name or birthdate.
- Use a firewall: A firewall is a network security system that monitors and controls network traffic. It can help block unauthorized access to a computer or network.
- Use antivirus software: Antivirus software can help detect and remove malware from a computer.
- Avoid clicking suspicious email attachments and links: Do not click on links from unknown senders, as they may contain malware.
- Back up essential data: Regularly back up important data, like documents, photos, and videos, to a cloud storage service or an external hard drive.
- Be cautious on social media: Be wary of clicking on links or downloading files from social media platforms, as they may contain malware.
- Secure your home network: Secure your home network with a strong password and consider using a virtual private network (VPN) to encrypt your internet connection.
- Educate yourself and your employees: Cyber threats are constantly evolving. Staying informed about the latest cybersecurity threats is essential. To achieve this, consider obtaining relevant certifications, such as those offered by Cisco. Utilizing resources like 200-301 Exam Dumps can also help you stay up-to-date on the latest security measures and best practices.
- Use Multi-Factor Authentication: It adds security by asking users to provide an additional form of identification.
Disclosure: This article contains affiliate links. If you sign up through these links, we may earn a small commission at no extra cost to you.
Frequently Asked Questions (FAQs)
Most security breaches result from social engineering, in which criminals use deception to persuade victims to divulge sensitive data, click on harmful links, or grant access to secure systems. Email or phone calls make the approach more credible.
Cyber threats can take many forms and are a worry for any firm. Attacks used to be disruptive and annoying annoyances, but in recent years, hackers have gotten more dynamic and aggressive in obtaining vital data and illegally accessing millions of dollars.
Yes, cyber threats are unethical and illegal. For example, the unauthorized access to, disruption, or theft of sensitive information from a computer system or network is considered a criminal act.
