Table Of Contents
What is Cybersecurity?
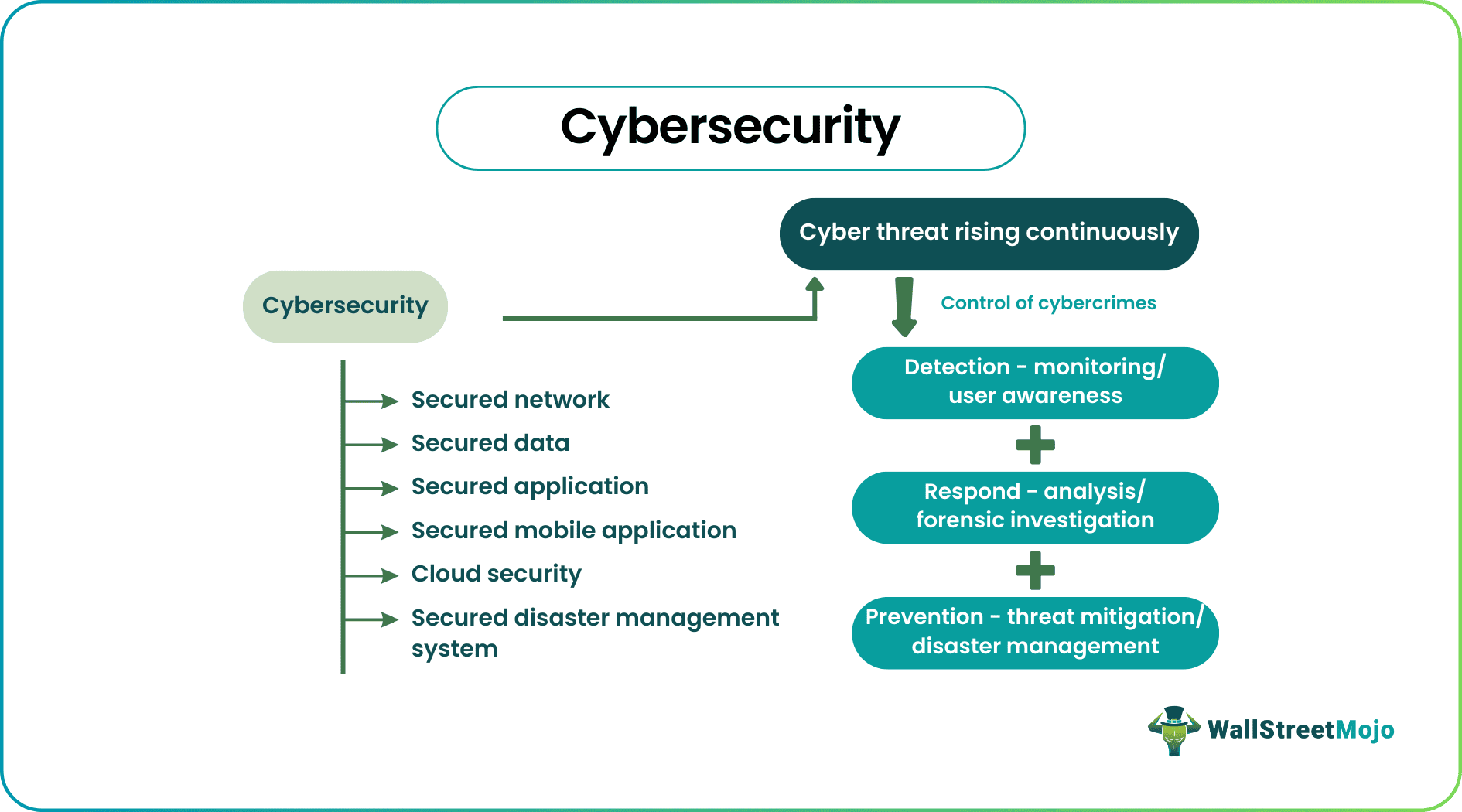
Cybersecurity safeguards computer systems, communication networks, and sensitive information from digital attacks. Securing cyberspace helps an organization protect itself from threats that result in long-term damage in terms of money and reputation. Such threats may come in internal or external forms.
Such malicious digital intrusion interrupts the entire business operation, resulting in a loss of revenue, time, and customer trust. Moreover, the changing economic and technological scenario is helping attackers devise new and innovative methods to launch attacks. At the same time, there is also continuous security measure upgradation to combat the offense.
Key Takeaways
- The cybersecurity framework helps combat digital crimes on an organization’s systems and communication networks.
- It enables the business to secure its system and sensitive information, which is prone to incorrect usage if they fall into the wrong hands
- and results in a loss of reputation and revenue. It sometimes causes the total business operation to collapse.
- It is necessary to keep and update the security system from time to time so that the business can continuously handle any new cyber threat, which is very common in the ever-changing technological environment.
Cybersecurity Explained
Cybersecurity helps organizations defend against technological crimes through multiple safety and surveillance levels, protecting sensitive data, programs, and communication networks. A cybersecurity analyst is an expert in detecting such threats and designing measures to implement and accelerate security functions.
Cyber safety operations have specific steps like detection, inspection, analysis, and prevention. Advanced organizations are also implementing collaborative testing methodologies such as purple teaming to validate their security measures by combining simulated attacks with defensive responses. The criminals mainly target sensitive data like names, addresses, Social Security Numbers, information related to credit cards, etc. Therefore, entities and individuals must have the basic knowledge and understanding of the type of cybersecurity threats and security measures required to handle them.
Choosing a reliable web hosting provider with strong security infrastructure, like Hostinger, can play a vital role in reducing cyber risks and ensuring data protection.
Types
Individuals or businesses may adopt various types of security methods to secure themselves.
- Network security – Adopting measures to protect computers and Wi-Fi networks.
- Data security – Protecting sensitive information like Social Security Numbers, credit card numbers, transactions, etc.
- Infrastructure security – Protecting business assets, infrastructure, computer systems, networks, etc.
- Cloud protection – Security related to storing data in the cloud, security during usage or processing, ensuring privacy, and adherence to regulatory standards.
- Educating end-users – It is essential to create awareness in the end user's mind regarding cybersecurity tools to help identify risks and methods to mitigate them.
- Application protection – An organization uses different applications to facilitate business operations. That application must have built-in security systems to protect the data against cybersecurity threats.
- Disaster management – Every business has arrangements to protect it from unforeseen situations like long power cuts, natural calamities, etc. These arrangements should be well-secured so that they are helpful during emergencies.
- Security of mobile applications – There are many updated safety measures and tools to protect mobile users from getting the data stored in mobiles hacked.
Examples of Cybersecurity
Let us understand the concept using some examples.
Example #1
Trust Capital is a finance company which into money lending and stock broking business. It is headquartered in California, the United States. It caters to small and medium-scale enterprises. Trust Capital has tied up with Guard & Protect, a security agency that protects both physical and digital information.
Trust Capital has discovered that specific data related to financial reports and stock prices have leaked into the market resulting in the company's stock price falling rapidly. Guard & Protect investigated the matter and found a severe breach of the central computer software of the finance department, leading to data transfer to competitors. Immediately the company shut down all activities for two consecutive days to fix the problem.
Example #2
Financial advisors are planning to upgrade clients' data security using various tools. It is vital because they continuously deal with confidential financial data, which is highly vulnerable to cyberattacks. In addition, more is needed to advise clients on investing and growing their money. Thus, they have devised protection methods for general, finance, and bank-related data. These tools will help keep data safe online.
Example #3
More businesses are investing huge sums into cybersecurity due to the rise in hackers targeting medium and small enterprises and extracting data for misuse. The Federal Bureau of Investigation (FBI) is highly concerned about this development because they are receiving a considerable surge in cyberattack complaints. These threats are resulting in massive losses in business.
Trends
The role of cybersecurity is increasing day by day because of the continuously changing business, economic and technological scenarios. Cybercriminals and violators are adept at devising new and improved methods to launch attacks. But at the same time, even the cybersecurity analyst is smart enough to identify, analyze and design ways to prevent a repetition of such frauds.
Some studies show that there has been a record rise in the data breach. The most vulnerable sectors are healthcare, retail, and public entity because these sectors have more access to general information. Cyber attackers use such data to extort money and change or destroy valuable services.
Even expenses related to cyber security breaches and security measures have reached as high as $133.7 billion. Thus, companies increasingly depend on cybersecurity tools to strengthen their surveillance systems and operations. Study shows that this market is expected to grow at a Compounded Annual Growth Rate (CAGR) of 9.7%.
Importance
The cybersecurity framework has gained massive importance in modern times in the following ways:
- Uninterrupted access to websites – The Internet plays a vital role today. Be it healthcare, manufacturing, education, science, innovation, etc.; the internet is everywhere. So, uninterrupted access to the site and providing authentic information is crucial. Safety in cyberspace ensures that.
- Public utility and defense – Defence and public utility services like water and electricity services should be highly protected from cyber attacks so that they work smoothly.
- Safe lifestyle – It ensures that we can maintain a secure lifestyle, free from fraud and unnecessary loss or tension.
- Safety of confidential data – Network security ensures personal organizational and individual data is protected against fraud and misuse.
- Maintain business ethics – Proper security measures help maintain business ethics since there are fewer breaches, and customers, employees, and stakeholders can continue to have faith in the process.
- Ensure information availability – A sound surveillance system ensures that information is available whenever needed.
Difference Between Cybersecurity And Information Security
Cybersecurity ensures safety in the cyber world, whereas information security ensures that confidential information and data is protected from all kinds of threat. However, there are some differences between them, as follows:
| Cybersecurity | Information Security |
| Related to a threat only in cyberspace | Related to the threat from any source |
| The process of protecting and preventing malicious software used to extract data | Helps to secure confidential information that can be a target for cyberattack |
| Secures data only in digital form | Secures data both in digital and physical form |
| Stops unauthorized access through password protection and encryption | Stops unauthorized access through password protection encryptions and locking cabinets/ lockers |
| A part of information security | Includes a vast basket of security procedures |
Disclosure: This article contains affiliate links. If you sign up through these links, we may earn a small commission at no extra cost to you.
Frequently Asked Questions (FAQs)
Coding is optional to learn this security method at an elementary level. But if someone wishes to take it up as a professional, learning to code in computer languages like Java, PHP, JavaScript, SQL, PowerShell, Python, and C is essential.
It is in high demand in today's technologically developed world. As more innovations come into the market, lives are becoming accessible, but the need for the internet is rising. Cybercriminals are using this opportunity to design malware to attack various processes to extract valuable data and confidential information for exploitation. Thus, the demand for security in cyberspace is rising.
Yes, working as a cybersecurity expert is possible remotely. It offers job opportunities that professionals can be done from home.
People inclined to learn new and updated technology will not find learning challenging. However, it requires effort and study. In addition, a lot of technical knowledge and skill has to be developed. Thus students from technical backgrounds find it more exciting and easy.
