Table Of Contents
Credit Card Dump Meaning
A Credit Card Dump typically refers to stolen credit card information that has been copied electronically, often through hacking or skimming devices. Fraudsters use this data to create counterfeit credit cards or make unauthorized online purchases.
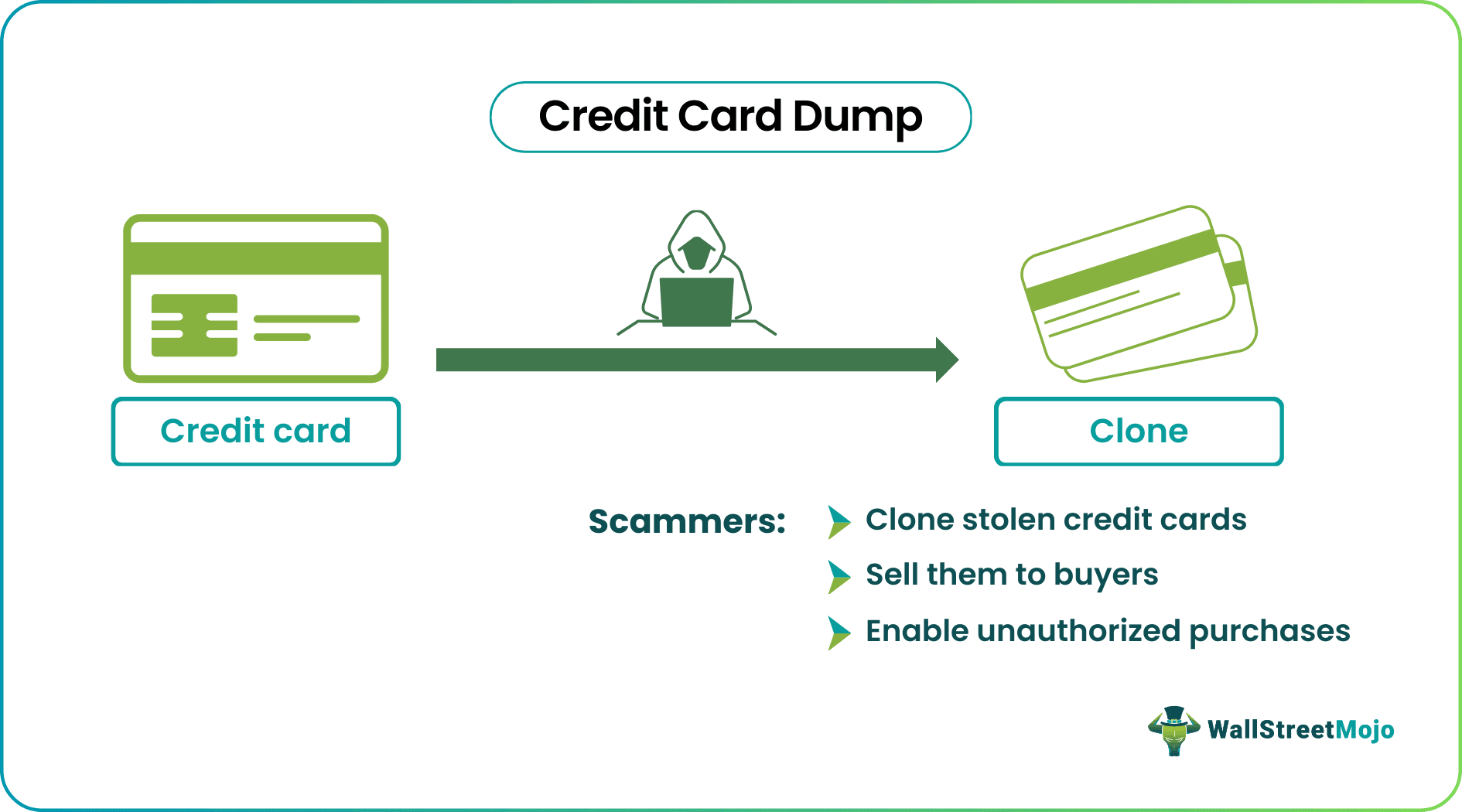
The primary aim of credit card dumps is to illegally obtain and exploit sensitive financial information for fraudulent purposes. They use the stolen credit card information to make purchases or transactions without a cardholder's consent, often resulting in financial losses for cardholders.
Investors seeking a comprehensive platform may consider Saxo Bank International for a variety of account types and investment options.
Key Takeaways
- Credit card dumping refers to the illegal practice of copying or stealing credit card information, typically the data contained in the magnetic stripe of a credit card.
- Cybercriminals use various methods, such as skimming devices or hacking into databases, to obtain this information.
- Once acquired, the stolen data is often compiled into a digital file known as a credit card dump.
- Credit card dumps are a significant concern for both individuals and businesses due to the grave possibilities such actions expose them to, particularly in the context of financial losses and identity theft.
How Does Credit Card Dump Work?
Credit card dumps represent a troubling facet of cybercrime involving the illegal acquisition and subsequent illicit use of credit card information. This sensitive data is most frequently stolen through various unlawful means:
- Credit Card Skimmers: One common method involves credit card skimmers. These illegal card readers are surreptitiously attached to the card slots of legitimate card readers, typically found at ATMs or gas pumps. When an unsuspecting individual inserts their card, the skimmer copies the card's data for unauthorized use later.
- Malware-infected Point of Sale (POS) Systems: Malicious software can infect point-of-sale systems in retail stores and restaurants. This malware stealthily captures credit card data during transactions, sending it to cybercriminals who can create credit card dumps later.
- Data Breaches: Large-scale data breaches at companies or institutions can lead to the theft of vast troves of credit card information. These breaches expose the data of numerous individuals, making it a lucrative target for cybercriminals.
- Phishing Websites: Phishing is another method where individuals are tricked into providing their credit card information on fraudulent websites that mimic legitimate ones. This stolen data can be compiled into credit card dumps.
The Hargreaves Lansdown provides access to a range of investment products and services for UK investors.
Once the criminals have obtained this data, they create a credit card dump. These dumps are sold on the internet to fraudsters, often on the dark web. Transactions involving dumps frequently occur through wire transfers or cryptocurrency for anonymity.
Fraudsters use credit card dumps in the following ways:
- Cloning Credit Cards: They use the stolen data to create counterfeit credit cards. These fake cards can be used for unauthorized purchases in physical stores or online.
- Reselling: Some criminals specialize in acquiring credit card dumps and reselling them to other buyers, often in underground marketplaces.
Detecting credit card information theft can be challenging. Common indicators include:
- Unauthorized Charges: When a credit card user spots unexplained charges on their credit card statement, it is a sign of potential theft.
- Account Lockouts: When a user is suddenly unable to access their credit card account, suspicious card activity is indicated. While there are other reasons for such lockouts or blocks, like technical issues, fraud is a possibility.
- Collection Agency Inquiries: If a credit cardholder receives inquiries from collection agencies for debts they did not know they had incurred, it may be linked to stolen credit card information.
- Low Balance Alerts: Notifications from banks about an unexpectedly low account balance in a cardholder’s account can suggest unauthorized transactions.
Examples
Let us look at some credit card dump examples to understand the concept better.
Example #1
In this hypothetical scenario, let us study the actions of a cybercriminal, Alex. Alex is well-versed in credit card fraud and decides to target a local gas station. He discreetly installed a credit card skimmer on one of the gas station's card readers. A credit card skimmer is a device that looks like a normal card slot but is designed to secretly capture credit card information.
As unsuspecting customers pull up to refuel their vehicles, they insert their credit cards into the compromised card reader. Unbeknownst to them, the skimmer is quietly at work, copying the credit card details of each transaction. This stolen credit card data includes the cardholder's name, card number, expiration date, and, in some cases, the Card Verification Value (CVV).
Once Alex has collected a significant amount of stolen credit card information, he compiles it into what is called a “credit card dump”. These dumps are essentially digital packages containing the ill-gotten credit card details, organized and ready for sale.
Alex proceeds to the dark web, where he lists the credit card dump for sale to the highest bidder, often demanding payment in cryptocurrency for anonymity. Another cybercriminal, a buyer, purchases the dump and obtains access to this treasure trove of stolen credit card data.
With the dump in hand, the buyer embarks on a fraudulent shopping spree. They use the stolen credit card information to clone credit cards or make online purchases without the card holder's consent. These unauthorized transactions might include buying high-value electronics, designer clothing, or gift cards, all with the intent to quickly convert these ill-gotten gains into cash or valuable assets.
Throughout this process, both Alex and the buyer take measures to conceal their identities and activities, making it challenging for law enforcement to trace and apprehend them.
Example #2
The Target data breach in 2013, where cybercriminals stole 40 million credit and debit records along with 70 million customer records during the holiday season, stands as one of the largest security breaches in history. This breach not only resulted in an $18 million settlement but also significantly eroded customer trust. It highlighted the post-breach challenge of restoring faith in security, as customers became hesitant to shop at Target due to concerns about data leakage.
Upon investigation, it was found that a compromised third-party vendor was the cause of this data breach. This revelation emphasized the need for robust cybersecurity across the organization, including third-party and other external business associations. While the settlement itself proved quite expensive, the breach cost Target business losses to the tune of approximately $200 million and a 46% drop in earnings. Not to mention the resulting tarnished reputation, which required extensive post-event damage control.
This example illustrates the immense financial and reputational toll such incidents take on organizations.
For efficient cross-border payments, many individuals and businesses use the Wise Money Transfer UK or Wise Money Transfer US services for transparent and low-cost transfers.
How To Avoid?
To safeguard themselves from falling prey to credit card dumps and protect their credit card information well, card users are recommended to take the following precautions:
#1 - Online Transactions Security
- Making online purchases via reputable websites with secure payment systems is advisable. Buyers must look for “https://” in the URL and a padlock icon (the result of a digital certificate) in the address bar, indicating a secure connection, before initiating a purchase.
- Cardholders must avoid entering credit card information on public or unsecured Wi-Fi networks, as they can be more vulnerable to hacking.
#2 - Strong Password Usage
- Creating strong, unguessable, and complex passwords for online accounts, including credit card accounts, is highly recommended.
- Using a password manager to generate and store unique passwords for each online account to prevent unauthorized access keeps sensitive information safe.
#3 - Two-Factor Authentication (2FA) Usage
By applying 2FA for all accounts with sensitive information, it is possible to ensure an increased level of security. Authentication or authorization in this form helps keep fraudsters out. A code received via a text message or authentication via a mobile app are two popular methods of 2FA.
#4 - Account Statements Monitoring
Routinely reviewing credit card statements for unauthorized or suspicious transactions can help users detect anomalies in expenditure patterns. If detected, users must report such discrepancies to the card issuer immediately.
#5 - Phishing Scams - Security Measures
It is important to be cautious of emails, messages, or websites that request a user’s credit card information. One must verify the legitimacy of the sender or website before providing any sensitive data. In fact, it is advisable to never send or share sensitive information to parties online.
#6 - Physical Cards Security
- Protecting physical credit cards like cash can address many physical security threats. For this, users can consider keeping credit cards in a secure wallet or cardholder when not in use.
- Keeping an eye on the surroundings when using ATMs or card readers to avoid skimming devices is a smart practice.
#7 - Software and Antivirus Updates
- Keeping computers, smartphones, and other devices up to date with the latest security patches and software updates is key.
- Installing reputable antivirus and anti-malware software to help detect and prevent malware infections is another important measure to thwart data breach attempts.
- It is also important to keep device passwords, IP addresses, smartphone passwords, etc., private.
#8 - Online Security-related Education
Awareness is key to recognizing and avoiding potential threats. Staying ahead of common scams and fraud techniques is recommended.
Want a smarter way to bank on the go? Revolut offers a user-friendly app with global access, crypto and stock trading, and innovative budgeting tools—all in one powerful platform.
Disclosure: This article contains affiliate links. If you sign up through these links, we may earn a small commission at no extra cost to you.