Table of Contents
Chain Of Custody Definition
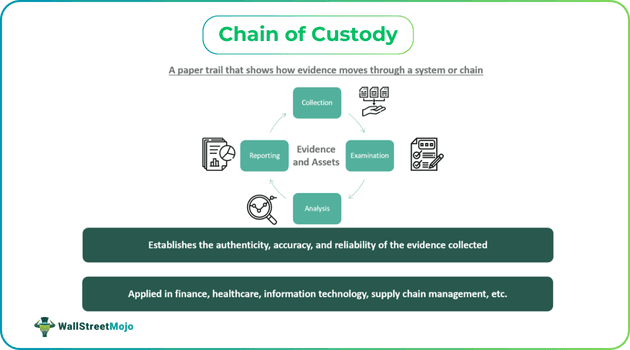
Chain of Custody refers to the documentation maintained in chronological order to track both physical and electronic evidence, including details about control, custody, transfer, and analysis, among other things, related to a specific event or case. This term applies to various fields, such as supply chain, law enforcement, healthcare, information technology, and finance, among others.
This logical sequence has multiple members, each playing a key role in recording, controlling, transferring, analyzing, and disposing of the evidence in question. If this chain breaks, the evidence may be lost, tampered with, or become inadmissible. When a proper trail is followed, it ensures accountability and transparency and maintains the integrity of analysis and reporting.
Key Takeaways
- Chain of custody is the set path that evidence follows from the moment it is collected to the point it is either handed over or reaches the point where it is disposed of.
- In finance, it can be accomplished through these four steps: data collection, examination, analysis, and reporting.
- It assists in recording, controlling, transferring, storing, analyzing, and disposing of financial and other evidence based on the field in which it is used.
- It is also relevant to asset tracking and management.
- Each step in this chain is essential, and omitting even one may lead to inaccurate data, contamination of proof, misleading paper trails, and corrupt data, among other issues.
Chain Of Custody In Finance Explained
Chain of custody in finance refers to the recording, documentation, and tracking of financial information, data, and records in a logical sequence. Both physical and electronic evidence pertaining to the financial records of an entity are gathered, recorded, stored, transferred, analyzed, and handed as required. Such recording and tracking enables auditors to execute audits, investigate accounting and financial records, and ensure a reliable audit process.
Evidence can get corrupted during financial audits if the chain of custody deviates from its defined path. This can result in a paper trail or digital reports coming in contact with more people than necessary. This is one of the reasons the chain of custody is meticulously preserved and followed.
Different entities may follow different paths to ensure the reliability of the chain of custody. As the evidence travels from one process or person to another, it is streamlined and verified for accuracy, which helps auditors audit, investigate, and arrive at reliable conclusions. This, in turn, facilitates the preparation of the final audit report for submission to stakeholders.
The chain of custody evidence runs the risk of contamination, manipulation, and alteration. It can also be tampered with or may even be lost in the process. Such incidents can happen accidentally or be executed intentionally. Hence, designing, recording, and tracking each step is crucial.
The chain of custody also applies to asset tracking. Every entity (financial institution, bank, trust fund, etc.) uses it to establish, oversee, and track asset movements. Many software solutions are available to make this process simple and hassle-free. By maintaining a proper chain of custody, companies ensure assets under management are identified, assigned, transferred, tracked, and handled well.
The chain of custody in forensics guarantees the preservation, collection, and processing of assets and evidence. Its absence leaves businesses and corporations in a tough spot, making them vulnerable to legal obstacles in data management problems.
Procedure
We know that the chain of custody is crucial across many fields. It follows a set process defined by relevant entities based on specific requirements. In this section, let us study the general procedure one can follow to ensure the reliability and authenticity of evidence and assets.
- Gathering data and evidence: This is the first step, where evidence, physical or electronic, is gathered through various internal and external sources. Once the data is acquired, it is identified or categorized, sorted, labeled, recorded (log entries), and stored.
- Evidence examination: Next, the relevant evidence is considered for further examination. It involves checking the authenticity and validity of the evidence. Unwanted documents may be eliminated at this stage. The evidence is further tested for relevance and accuracy.
- Analysis: Now, the relevant authorities have accurate data and evidence in hand. They perform in-depth analysis to derive useful insights through legally justifiable techniques and methods. It is during this process the evidence becomes proof of the underlying objective and agenda. The analysis supports the basis of the audit. In finance, such analysis shows money flow, hidden accounts, the source of fraud and malicious activities, etc.
- Reporting: At this stage, based on the information derived from the evidence in custody, relevant entities create a final report describing the errors and inconsistencies and highlighting the issues detected. Such reports typically include a chain of custody statement, outline the identified issues, and list the tools used in the analysis. If required, recommendations for further evaluation and measures that can be taken are listed.
Examples
From the discussion above, we can see that the chain of custody is crucial from the financial, commercial, business, and legal viewpoints. In this section, let us study some examples to understand this topic in greater detail.
Example #1
Suppose Angela, the bank manager of FirstFund Bank in Texas, suspects ongoing fraudulent activities in her branch. According to the bank’s policy, she appoints an auditor, Gemma, to perform an internal audit.
Gemma and her team members collect evidence, gathering every piece of document, statement, bill, and invoice from the previous year. Her team then compiles the records for analysis. Gemma uses a chain of custody form to note all the evidence collected through this process.
Gemma’s team then moves to the next step, where it examines the evidence before undertaking an in-depth analysis. She follows the paper trail and flow of money. Whenever she encounters issues, she approaches Angela, who gives her the required information.
During the audit, Gemma noticed that certain transactions did not match the corresponding paperwork. Upon further investigation, she found that the accountant had been siphoning off significant amounts from the bank to a savings account.
Gemma submits her audit report to Angela, who then initiates legal action against the accountant.
Example #2
A Deloitte article published in February 2024 discussed the regulations surrounding cryptoasset custody in the United Kingdom, given that certain key changes were to take place soon. The Financial Conduct Authority (FCA), through a Discussion Paper (DP), proposed a system for regulating cryptoassets, where the focus would be on security tokens and regulated stablecoins.
To implement this, the Client Asset (CASS) Sourcebook will be used as the basis for custody rules. The rules involve:
- Segregation of Firm and Client Assets
- Adequate Organizational Arrangements to Minimize the Risk of Loss
- Use of Third Parties
- Accurate Books and Records
- Regular Reconciliations of Client Assets
- Client Disclosures
Given this background, let us see how the chain of custody comes into play here. For cryptoassets, the chain of custody revolves around the recording, documentation, and tracking of these assets as they move from one stage to another. These include issuance, trading, and storage. This ensures the authenticity, accuracy, and reliability of these assets. It means no entity or individual can tamper with them or access them without authorization.
Hence, the proposed system will work on custody principles that support the chain of custody requirements, which is digital asset custody in this case. It will also state how cryptoassets should be managed in the given regulatory environment.
Importance
In this section, we will see why it is important to have a proper chain of custody.
- Paper trail: It establishes the proper route the evidence must follow, during which each member does their job from recording to disposition.
- Recording consistency: It is a logical sequence, making the entire procedure swift and easy. Technically, it indicates that no process or step can be skipped.
- Evidence preservation: Evidence may become inadmissible from a legal standpoint (in civil and criminal cases) if the chain has not been followed properly.
- Evidence quality: It represents the appropriate gathering of evidence and maintaining its quality and precision. Such evidence may include financial information, technological records, supply chain movements, etc.
- Audit support: Typically, auditors rely on the efficiency of this chain as they believe that organizations will employ prescribed procedures for the proper storage of evidence, making interpretation hassle-free.
- Asset management: It is a chronological paper trail showing accurate records of assets, covering their lifecycle, including location, access, etc.
